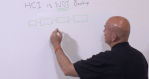The motivation to protect cloud-based applications is different from on-premises applications. Cloud providers like Amazon do a good job of providing a basic level of data protection, including resilience from media failure, snapshots, and multi-cloud replication. The most common cause…